As more computer users flock to the cloud to store their information, the amount of personal information online is increasing at an exponential rate. Along with that growth is the increased risk associated with the exposure of private and sensitive information over the internet. When we upload personal data to services like Google Docs or transfer our emails to Gmail, we face an added level of risk exposing our personal and confidential information on the internet. I’ve been meaning to write this article for quite some time, but never got around to it. A recent comment by one my readers confirmed my reservations over the increased use of online services to save and work on potentially sensitive and private information.
In this article I will summarize some of the things that I do and that you too can repeat to reduce the likelihood of a breach to your personal information online. If you have a method you use and would like to share it or have other information that is useful please post it below. Browse safely.
1. Use Trusted Devices
Although elementary in nature, how many times have you signed on to your Facebook, Twitter, Gmail, or another account on a computer other than your own? If you know anything about keyloggers or other forms malware, you would think twice about signing on with any computer.
The bottom line is unless you trust the device that you are on, don’t use it. So how do you access you accounts if you have no choice? Please read #2 & 3.
2. Use Travel Accounts When Away from a Trusted Device
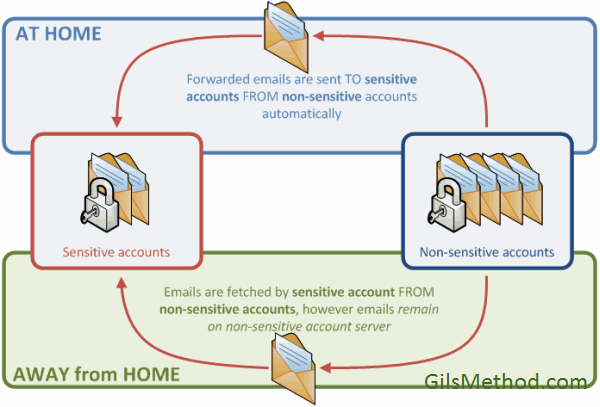
Travel accounts? What the heck is that? Like many people I have accumulated enough email addresses to warrant a spreadsheet that lists all of the user names and passwords…yes…that many. In reality there are 2 accounts that I use for sensitive information (bank statements, bills, receipts, personal information, etc) and those two use very strong passwords (see #3). The rest of the accounts use strong passwords as well, but contain information that is less sensitive (comment updates, subscriptions, etc). These accounts are normally setup to forward email to the sensitive accounts.
When I travel I disable the forwards to the sensitive account from the non-sensitive accounts and then enable fetching of emails on the sensitive account from the non-sensitive account. I then make sure that the leave emails on server option is enabled. This ensures that emails are fetched by the sensitive account, but remain in the non-sensitive account so that I can read the messages while traveling.
Refer to the diagram below for a visual explanation of this information.
3. Would the Strong Password Please Stand Up?
Your daughter’s birthday or sparky’s name are not very good candidates for passwords. Instead try something like 1b45Hd-45gO as a password – oh it’s too long? Well just so you have an idea of how weak sparky or someone’s birthday is, I have listed how different password types vary and the length of time it takes to crack them by a supercomputer.
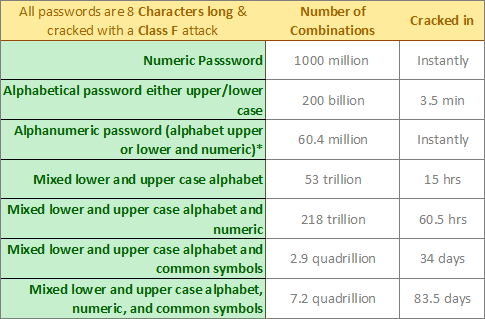
*Denotes that the password is 5 characters in length
A Class F attack is an attack performed by a supercomputer which can generate 1,000,000,000 password combinations per second. Of course there aren’t supercomputers run by individuals for the sole purpose of cracking passwords, but considering that a fast dual processor computer can generate 100,000,000 password combinations per second one has to be aware of the simple fact that your password can be cracked. Luckily there are different controls in place that prevent passwords from being tried again and again. For instance there are several web portals that only allow 3 password tries, if you fail on the third try your account is either locked until verified or locked for a number of hours.
Yes, an eight character numeric password will be cracked instantly by almost any computer. A password using alphanumeric characters and symbols will take approximately 83.5 days to crack. Conclusion use a longer password when possible and make sure to use the a combination of numbers, upper/lower case letters, and finally symbols.
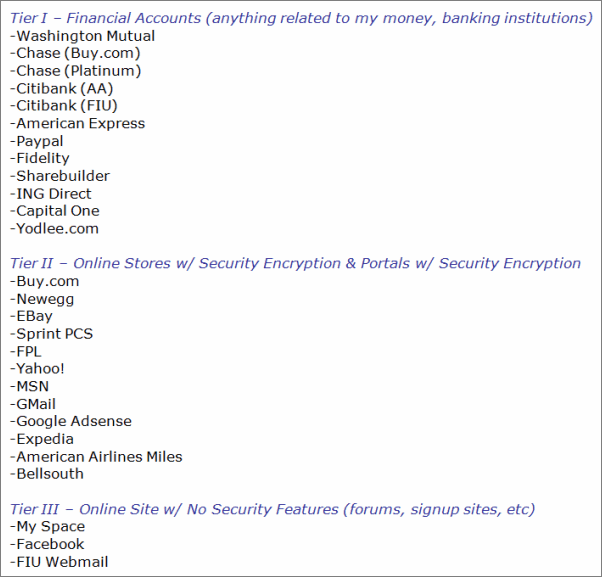
4. Tier Your Passwords
Another strategy that I use to help protect my password is password tiering. Password tiering is simply classifying certain websites, applications, and other password driven devices into tiers. I currently use 3 tiers for my passwords. The reason for password tiering is so that you don’t use the sensitive email account password to log onto say, Twitter or another website that does not support HTTPS. The same applies for online banking, you certainly don’t want your banking password to be the same as your Digg account do you?
Below you will find an example of the tiers that I use for my passwords, you are free to duplicate it or come up with your own.
5. Use HTTPS when Possible (otherwise follow #3)
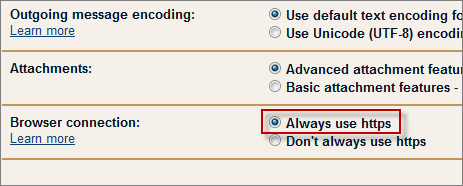
Every time you sign on to Gmail you are transmitting your user name and password via an encrypted browser connection, which means that if intercepted the information could be used by someone else. You can tell Gmail to use HTTPS connections only.
To enable this feature go to Settings > General and select Always use https, click the Save Changes button. Next time you visit gmail type;
You can confirm your secure connection by verifying the favicon located on the address bar (see #7) and by locating the small lock in the browser status bar (bottom right of the window – see below).
Note: The location of the lock icon varies by browser. I used Firefox 3.1 for the screen shot above.
6. Secure Your Mobile Phone
Until a recent scare I didn’t have a password to get into my BlackBerry, I considered it a nuisance and an additional step to use my phone. When I lost (caught misplaced) my phone a couple of weeks ago I had a panic attack. My browser was setup with all of my accounts for auto log in, Google Calendar Sync had access to my calendar, and the Gmail App had access to my sensitive email account. Luckily I found that the phone had fallen out of my pocket and was safely tucked under the driver seat of my car.
This scare prompted me to enable password protection to my BlackBerry. You can enable password protection by navigating to Options > Security Options > General Settings and enabling the password prompt. Note: You will be able to make emergency phone calls without the password.
The proliferation of mobile phones with internet access increases the chances of phone loss, but more importantly the loss of privacy and personal information. I urge all of my readers to learn from my experience and secure your mobile phones.
7. Backup Files from the Cloud
As we place more and more data on the cloud we need a way to ensure that we have a backup of that data locally. Since I mainly use Google Docs and Gmail on the cloud I will go over some of the steps you can take to safely backup those services locally. If you would like information on a specific service not mentioned here, please drop me a line in the comments below or via email and I’ll try my best to cover it in a future article.
I found that one of the easiest and surest ways to backup a Gmail account was to use Outlook Express or Outlook with the IMAP protocol to download your messages to a local store. I have covered this method in a previous article that can be found by following the link below.
Transfer Your Outlook Emails to Gmail
To backup your Google Docs files use the Google Documents backup utility which can be downloaded from the GDocBackup website.
I will include detailed instructions for using GDocBackup in a future article.
8. Use a Safe Browser with Extensions
I personally use Firefox because it can be customized to my needs using add-ons that can be downloaded for free. However one of the reasons I really like to use Firefox is because of its security and safety. Some of those features are highlighted below.
Anti Phishing/Malware – this is one of those features that are extremely useful. Ever get an email from a Paypal wannabe? How would you know? Firefox alerts you when you visit on of these phishing sites and it really does a good job of it.
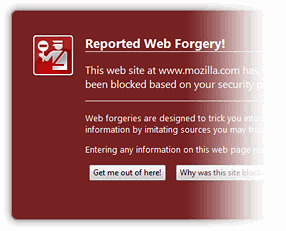
website Identification
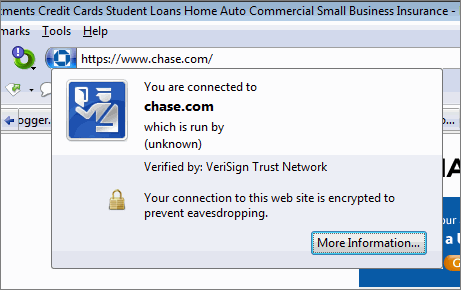
Aside from the lock designating a secure connection, as mentioned in #3 above, Firefox provides users with additional validation for the site that they are visiting. By clicking on a website’s favicon a pop-up window will appear with information about the identity of the website being viewed. When the More Information button is pushed the you will be able to look at the number of times you have visited the website and whether or not passwords are saved for that domain. So next time you are at a website and it seems fishy, click on the favicon and discover the site’s true identity.
Firefox Plug-ins I Use to Keep Me Browsing Safely
I use WOT (Web of Trust) which indicates, based on user feedback and other databases, whether or not the site being visited is safe or not.
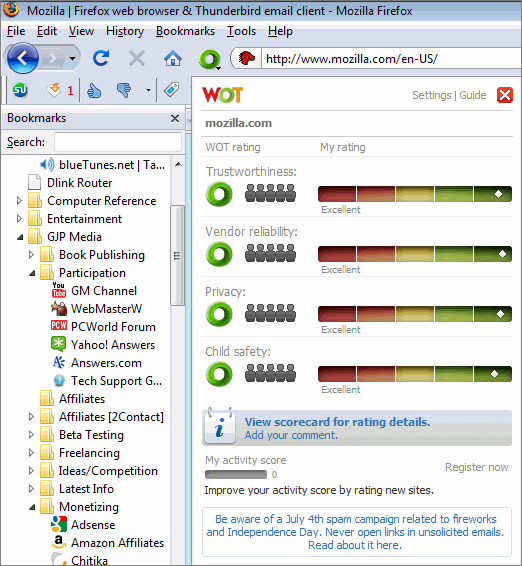
Download WOT from the WOT website
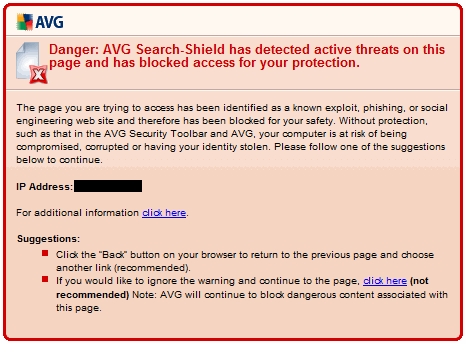
I also use AVG’s Search-Shield plug in which alerts me of potential threats when I’m searching the web. The screen shot below illustrates the dialog box you will see if you attempt to access a website that is deemed unsafe by AVG.
Now that I’ve covered some of the steps that I take to secure my information in the cloud, do you have any tips to offer?
Password combination information obtained from lockdown.co.uk